Tutorial: The Complete Guide to Modern Identity and Access Management
1. Identity — the “Who”
Identity is the digital representation of a person, service, or device.
- Example: “Rajesh with email
rajesh@example.comand employee ID1234.” - Why it matters: Every other IAM concept builds on knowing who is accessing resources.
2. Authentication — Prove the Who
Authentication verifies identity.
- Methods: Passwords, OTP, biometrics, WebAuthn/Passkeys.
- Example: Logging into Gmail using a password + OTP.
- Best Practice: Use MFA (multi-factor authentication) for higher security.
3. Authorization — What They Can Do
Authorization determines permissions after login.
- Models:
- RBAC (Role-based): Admin, User, Guest.
- ABAC (Attribute-based): Department = HR, Location = Tokyo.
- PBAC (Policy-based): If
role=Managerandlocation=HQ, then allow.
- Example: A doctor can view patient records; a receptionist can only schedule appointments.
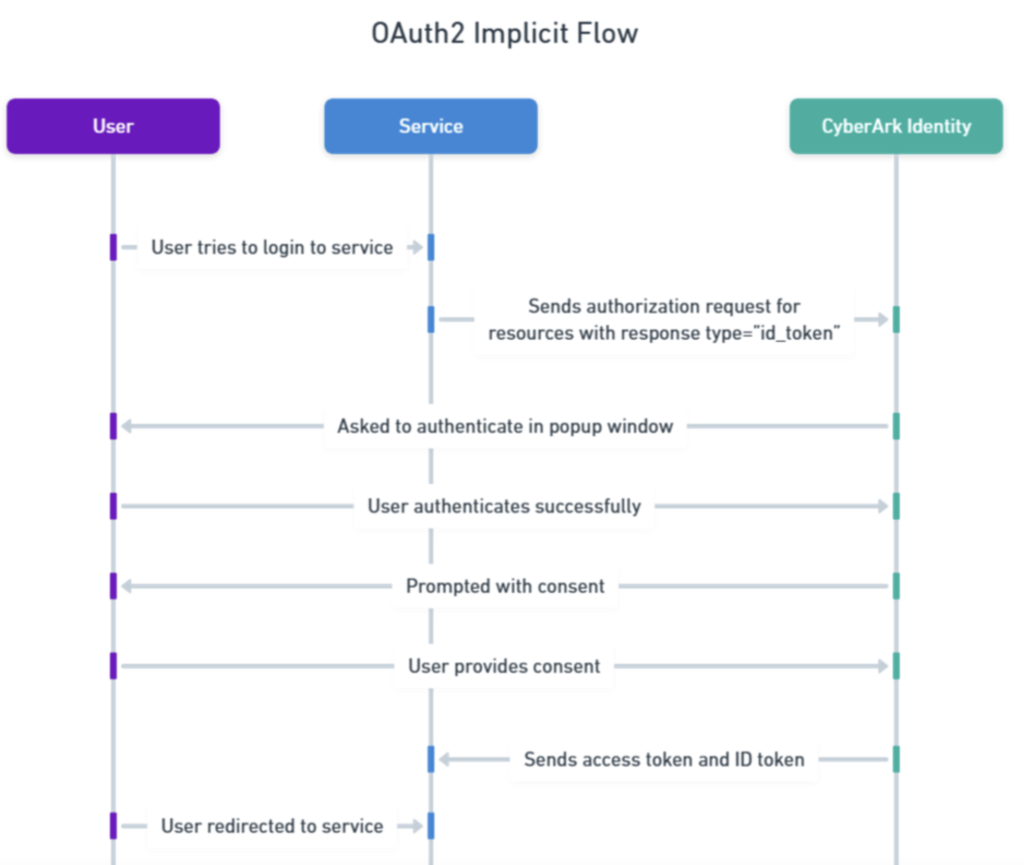
4. OAuth 2.0 — Delegated Authorization Framework
OAuth2 lets apps access resources on a user’s behalf.
- Tokens: Access Token, Refresh Token.
- Example: Canva asks permission to access your Google Drive photos. You approve → Canva gets an access token.
- Note: OAuth2 ≠ Authentication. It’s mainly about authorization.
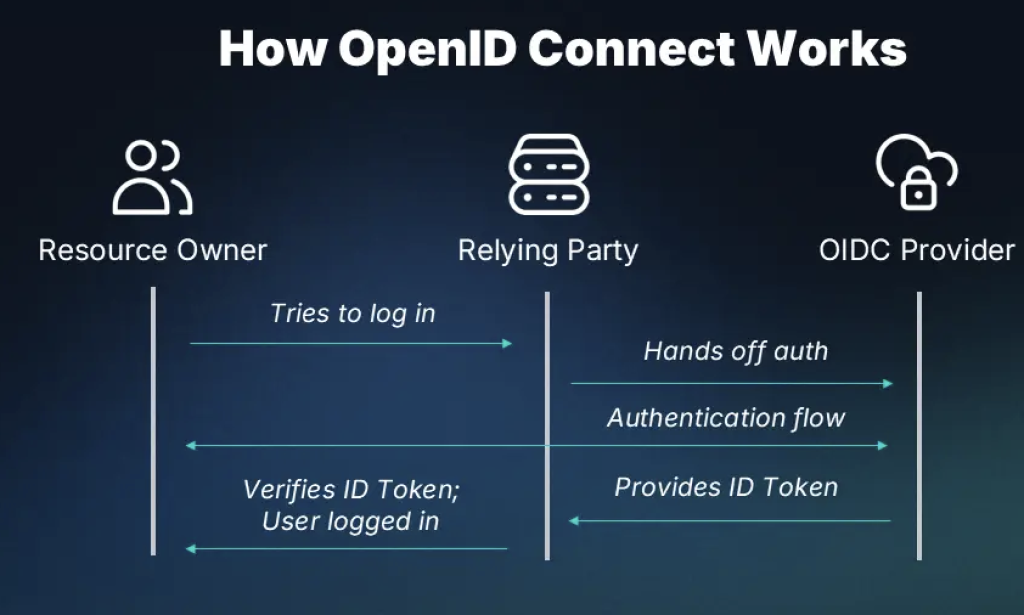
5. OIDC (OpenID Connect) — Authentication on Top of OAuth2
OIDC extends OAuth2 to handle authentication + identity.
- Tokens:
- ID Token → JWT containing user info.
- Access Token → permissions for APIs.
- Example: “Sign in with Google” → OIDC gives the website Rajesh’s identity (email, name).
6. Tokens — The Currency of Access
Tokens are proof of identity and permissions.
- Types:
- Access Token → access APIs.
- Refresh Token → get new tokens.
- ID Token → prove who the user is.
- Example: Access Token lets Slack read your calendar data after you log in via Google.
7. JWT (JSON Web Token)
JWT is the format most tokens use.
- Structure:
Header.Payload.Signature. - Claims inside = user info, expiry, roles.
- Example:
{ "sub": "1234567890", "name": "Rajesh", "role": "Admin", "exp": 1712345678 }
8. Claims — Identity Details in Tokens
Claims are facts about the user/system embedded in tokens.
- Example:
sub=1234,email=rajesh@example.com,role=Admin. - Use case: APIs read claims to enforce role-based authorization.
9. Identity Providers (IdP)
IdPs authenticate users and issue tokens.
- Examples: Google, Azure AD, Okta, Auth0, Keycloak.
- Role: Trusted source of authentication.
- Example: You log in to Zoom with Google — Google is the IdP.
10. IdentityServer
An IdP implementation for .NET apps.
- Example: A company builds its own login system using IdentityServer instead of outsourcing to Google or Okta.
11. SSO (Single Sign-On)
Login once → access multiple apps.
- Example: Logging into Google once gives you access to Gmail, Drive, YouTube.
- Enabled by: OIDC, tokens, centralized IdPs.
12. Federation — Trust Across Domains
Federation lets one identity system trust another.
- Standards: OIDC (modern), SAML (legacy, XML-based).
- Example: Spotify lets you log in with Facebook → Facebook acts as the trusted IdP.
13. SCIM (System for Cross-domain Identity Management)
Handles user provisioning and de-provisioning.
- Example: When a new employee joins, SCIM auto-creates accounts in Slack, GitHub, Google Workspace.
14. PKCE & Session Management — Extra Security Layers
- PKCE: Secures OAuth2 flows in mobile/web apps.
- Session Management: Handles login state, re-authentication, and global logout.
- Example: Revoking your Google session logs you out of all Google apps.
15. Consent & Scopes — Granular Access Rights
Scopes define what an app can do.
- Example:
calendar.read→ read-only calendar.calendar.write→ modify calendar.
- Consent screen: User approves scopes during OAuth2 login.
16. Introspection & Revocation
- Introspection endpoint → APIs check if a token is still valid.
- Revocation endpoint → Users or admins revoke access.
- Example: You revoke Canva’s access to Google Drive → Canva’s tokens are invalidated.
17. API Gateway / Policy Enforcement
API gateways enforce token validation, scopes, and claims.
- Examples: Kong, Apigee, AWS API Gateway, Envoy.
- Example: An API gateway checks if Rajesh’s access token includes
role=Adminbefore allowing an update.
18. Zero Trust — Continuous Authorization
- Principle: “Never trust, always verify.”
- Access is continuously re-validated based on identity, device, location, risk.
- Example: Even after login, your bank re-checks identity if you try a large transfer.
✅ Summary in One Line
Identity → Authentication → Authorization → OAuth2 → OIDC → Tokens (JWT, claims) → IdPs (Google, IdentityServer) → SSO/Federation → SCIM → PKCE & Sessions → Scopes/Consent → Introspection → API Gateways → Zero Trust